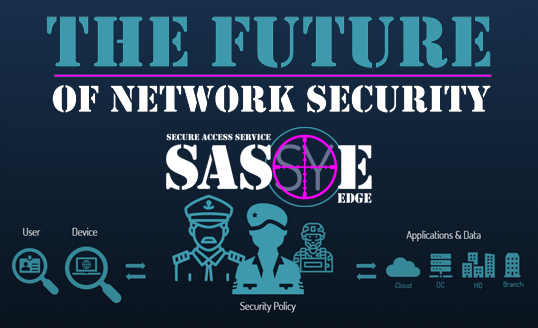
The Future of Network Security
In short, a SASE architecture identifies users and devices, applies policy-based security, and delivers secure access to the appropriate application or data.
So that’s a lot of fancy words, how does it translate to real life. Firstly some facts from Gartner:
- More user work is performed off of the network than on the network
- More applications are consumed via SaaS than consumed from enterprise infrastructure
- More sensitive data is located outside of the enterprise data centre in cloud services than inside
This presents growing challenges that ultimately form the tops use cases for SASE:
- Ensure that people have access to the right information, no less and no more
- Ensure a secure connection to company data, from whatever location it is accessed
- Prevent unintentional or unwanted data movement
- Gain visibility into high-risk users and high risk unsanctioned cloud applications
- Protect trusted users and devices from malware and other web threats in the cloud
Your SASE Journey
It may not be obvious where to start with your SASE journey, it incorporates SWG, CASB, DLP, ATP, ZTNA, VPN, FWaaS and more! We’re on hand to discuss the options but in our experience, Netskope, Okta and Crowdstrike are cloud borne security powerhouses that facilitate a fast and effective route to a SASE future. Being leaders in the sector, in partnership they help:
- Enable your workforce to safely access cloud services from anywhere, on any device.
- Give IT and Security teams visibility into all user behaviour, from login to logout.
- Monitor, validate, investigate and remediate anomalous behaviour.
- Protect sensitive data and user identities from internal and external threats.
As always, we are on hand if you’d like to know more.





