
Hopefully that reminder doesn’t trigger PTSD from late nights, long weekends and months of lost security operational time dealing with remediation of these zero-day vulnerabilities. It’s not only the stress of unexpected, unscheduled remediation effort, but also the impact on forward-thinking strategic security projects that these incidents incurred.
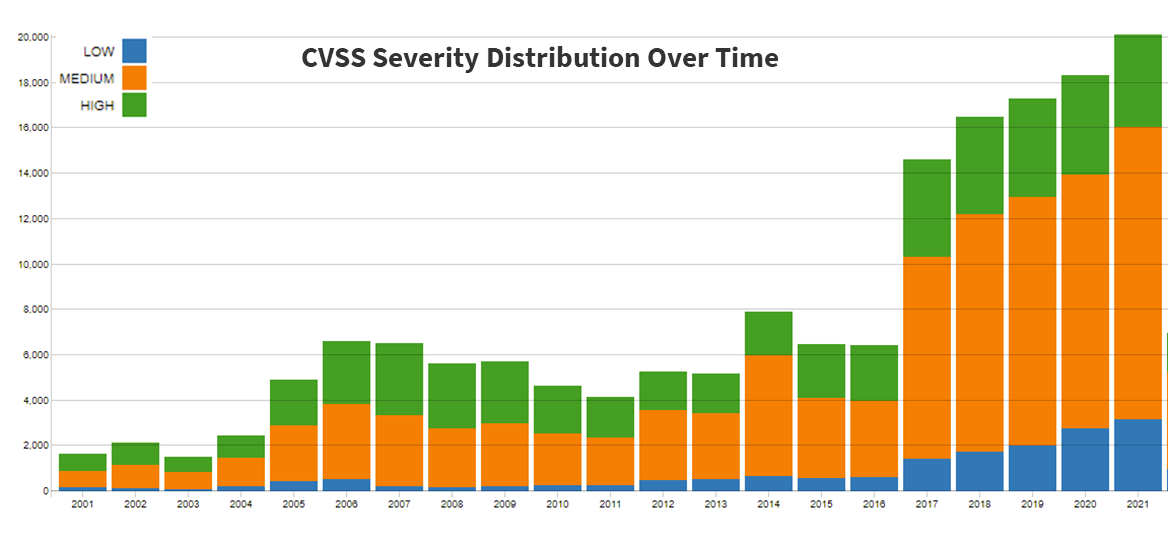
The bad news; this graph from NIST suggests we should only expect more vulnerabilities as a whole and more critical 0-day attacks that pose a risk that can’t be ignored. We call the big ones ‘Celebrity Vulnerabilities’ because they often hit the headlines and provoke a scramble to patch an exploit.
So how do you prepare for the next zero day to best avoid those unexpected late nights and long weekends reactively remediating? There’s no magic solution that means you’ll never have to spend time dealing with vulnerabilities again, however there is technology and process that significantly reduces the amount of IT and Security team effort required to keep on top of vulnerabilities and remediate the big ones efficiently to keep ahead of the attackers.
Policy and Process:
Vulnerability management is a foundation of cyber resilience. It’s front and centre in best practice frameworks from Cyber Essentials to ISO27001 to NIST CSF and CIS 18 CSC. A crystal ball to show when, what and how much effort the next 0-day will absorb would really help, but the reality is, you simply have to be prepared. All the frameworks encourage you to:
- continuously identify where your vulnerabilities exist,
- prioritise your remediation effort,
- apply fixes quickly,
- use automation where possible.
Technologies:
If you implement the right tools with sensible automation, ultimately risk is reduced faster with less time spent reactively remediating, meaning more time to focus on driving your security plan forward. Rapid7 IVM and Automox are Saepio’s tools of choice. They have joined forces to enable full-cycle vulnerability management by automating the manual tasks in traditional patching and remediation routines.
With Rapid7 continuously finding vulnerabilities in your environment and fuelling Automox with prioritised information to trigger automated patching, the volume and speed of vulnerability remediation is increased which in turn helps hit the best practice recommendations.
‘The impact and likelihood of adverse reactions to patches are lower than the impact and likelihood of a bad actor attempting to exploit the vulnerability’. CISO of Capital One Bank
Contact Us
Don’t hesitate to reach out to our solutions team. Simply call us on +44 (0) 1494 216 061 or drop us an email on contact@saepio.co.uk alternatively, you can submit a form on our contact page.



