“How can you build trust?” you may be asking. Inspecting different types of traffic and signals like device health (is this device up to date, does it have our EDR agent installed and running), or location, could be used to make a confident decision on access.
Compare this to a “traditional” castle and moat style architecture, where trust is established at the point of access to a resource. Just connect in with a VPN and gain access to resources on the network, in a fairly simple transaction. Zero Trust aims to augment this and “Never Trust, Always Verify”, using more signals to make more fine grain decisions on what resources are accessible for a contextual decision.
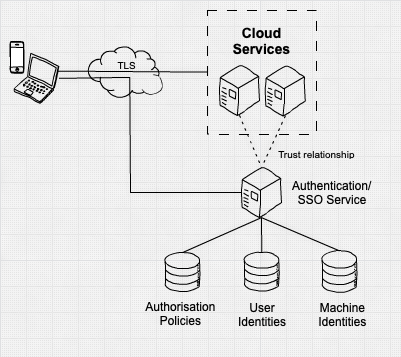
Saepio are a big fan of the below NCSC high level Zero Trust architecture diagram, which gives us an idea of the comparison to a more traditional architecture diagram. It’s key to note the important factors of user identity, machine identity and an authorisation policy, often based on what resource is being accessed;
So, we know a little bit now about what Zero Trust Network Access actually is, what are the benefits in light of the risks we’re seeing?
Tackle modern threats
At Saepio some of the main challenges we see enterprises dealing with often involve a compromised device or user account being used to access systems. Putting the majority of your security controls on the boundary of your network makes it difficult to detect an attacker if they successfully breach that first layer of defence.
In a zero-trust model, every action a user or device takes is subject to some form of policy decision. The user may not even be aware of it, but it allows the organisation to verify every attempt to access data or resources, making life harder for an attacker.
Better insight into your services and devices
Zero trust often brings enhanced monitoring capabilities through a host-based approach, which gives great insights into events on user and devices and servers, and a detailed picture of what is happening. More than ever, use of cloud and web services mean inspecting TLS traffic can be difficult, so maximising log and data collecting is key.
Make life easier for users
Some zero trust security controls can enable a much better user experience. Building authentication services to build in SSO or biometrics can reduce credential use and enable smart, secure systems which are easier to access. Private access solutions can also reduce VPN usage and leverage modern networks to speed up access to resources.
Collaborate with third parties easier and more securely
Greater insight and control over data access enables fine grain authentication to external systems and federating third parties in your systems. Sharing very specific sets of data becomes easier, simplifying security policies but increasing the level of collaboration possible.
Get the most out of security platforms
Lots of Saepio clients are investing in best of breed security platforms, often augmenting a Microsoft or Google investment for collaboration and mobility. Most of these security platforms come filled with capability to help enable a successful zero trust network access deployment, through prebuilt integrations, data sharing and shared decision making engines.
Now, with everything comes some challenges. One of those is that zero trust isn’t a cookie cutter standard, or a specification that vendors can design products and services against. It’s an approach to designing an architecture, which means it can be difficult to know that you’re doing the “right thing”. Not all technologies and services are suitable for zero trust either.
Creating an architecture that works for you, and choosing the right platform to enable a comprehensive Zero Trust Network Access strategy, is something we’re pretty good at here at Saepio. If you need some direction, why not attend our event on the 28th of September together with Crowdstrike, Okta and Netskope – three incredible technology providers who have one of the most compelling Zero Trust integration stories.
Contact Us
Don’t hesitate to reach out to our solutions team. Simply call us on +44 (0) 1494 216 061 or drop us an email on contact@saepio.co.uk alternatively, you can submit a form on our contact page.




