Still the favourite attack vector for malicious attackers, email remains the number one threat vector for initial compromises when analysing the source of data breaches for the tenth year in a row. As always, attackers are looking for new ways to avoid detection, circumvent defences and lessen the burden on URL’s or filetypes which have become known to be risky.
when analysing the source of data breaches for the tenth year in a row. As always, attackers are looking for new ways to avoid detection, circumvent defences and lessen the burden on URL’s or filetypes which have become known to be risky.
Across our client base at Saepio we’ve seen rises in emails that rely on coercion and familiarity rather than embedding payloads or bad URL’s. An example that was particularly sophisticated made it challenging even for a suspicious employee to question.
An attacker had been embedding email trackers which pulled back location data and was able to monitor where a CFO was, cross referencing it with open-source information from LinkedIn and Twitter. The company had announced participation at a finance leaders conference on LinkedIn but not been explicit about the date or time speakers would be giving their presentations.
Using location data, the attacker was able to see when the CFO had arrived on location, waited a few hours, and then emailed a senior finance leader with instructions.
“Hi xxx,
As you know I’m at xxx conference and about to go up on stage to speak. I’ll be unavailable for a few hours but need you to speak to xxx at xxx about payment we need to make for an engagement they’ve run for us.
Can I leave this with you? His number is…….”
No payloads, no URL’s, no attachments. Using a lookalike domain and genuine information, you can see how this would lead to a successful attack and payment made to a third party.
Having a comprehensive business email compromise strategy is one of the best ways to mitigate cyber risk. A well configured secure email gateway, well protected email identities through DMARC, empowering staff through training to spot risks and now, using machine learning to give them dynamic context-driven banners to highlight risks are all areas we consider crucial.
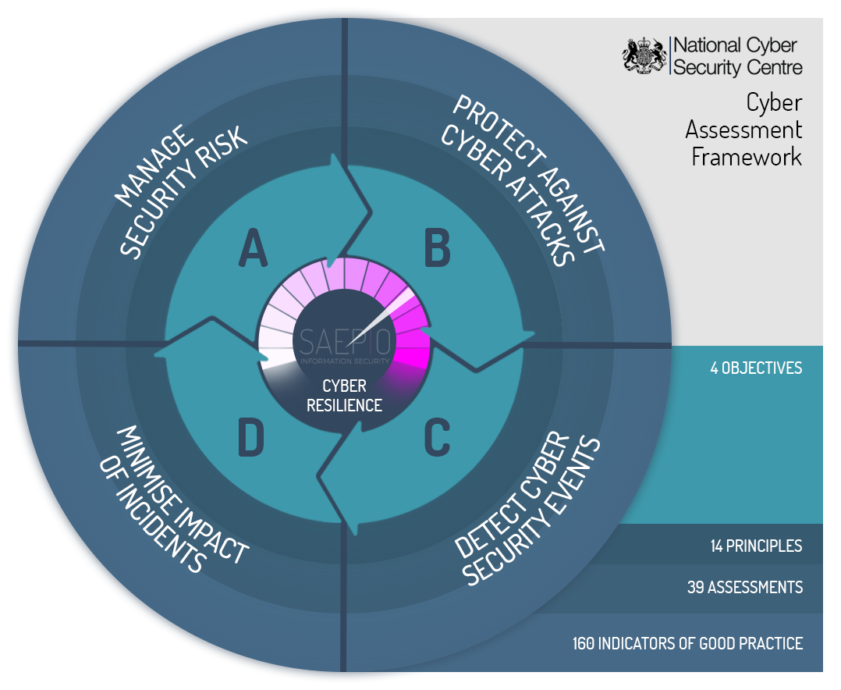
At Saepio we’re big fans of the NCSC’s Cyber Assessment Framework (CAF), underpinning the UK government’s ten year cyber strategy. We’d recommend spending some time evaluating how email feeds into the key objectives in the CAF and if you’re not sure on where to start, do reach out to Saepio and we’ll be happy to help.
Contact Us
Our solutions specialists are always on hand to run you through the results or provide a workshop on taking the results and turning them into meaningful action. Simply call us on +44 (0) 1494 216 061 or drop us an email on contact@saepio.co.uk alternatively, you can submit a form on our contact page.




