Cyber Threat Report Insights
Ransomware operators have been observed by CrowdStrike to be leveraging both Nation State APT style techniques, but also more traditional phishing and human vulnerability exploits. CrowdStrike’s tracking of eCrime groups and their behaviours is a large feature in their Global Threat Report 2021 and we highly recommend digesting it. The insight into the behaviours and groups to be wary of is truly informational and not sensationalised which is useful in helping plan mitigation strategies both on a technological and process level.
The high-level outcomes that I got from it and I hope you do too are;
- How state-sponsored adversaries infiltrated networks to steal valuable data on vaccine research and government responses to the pandemic.
- How criminal adversaries introduced new business models to expand their “big game hunting” ransomware activities — and made them even more potent with the addition of blackmail and extortion techniques.
- How both eCrime and targeted intrusion adversaries stepped up their development efforts, deploying a variety of inventive new methods to evade detection and confound defenders.
Crucial Takeaways
If you can’t see it, you can’t protect it. For security teams operating in today’s environment, visibility and speed are critical for blocking attackers that have the capability and intent to steal data and disrupt operations. Security teams must understand that it is their responsibility to secure their cloud environments, just as they would on-premises systems. They must establish consistent visibility for all environments and proactively address potential vulnerabilities before they can be leveraged by attackers.
Protect identities and access. Organisations must consider multifactor authentication (MFA) on all public-facing employee services and portals as mandatory. In addition to MFA, a robust privilege access management process will limit the damage adversaries can do if they get in and reduce the likelihood of lateral movement. Finally, Zero Trust solutions should be implemented to compartmentalise and restrict data access, thus reducing the potential damages from unauthorised access to sensitive information.
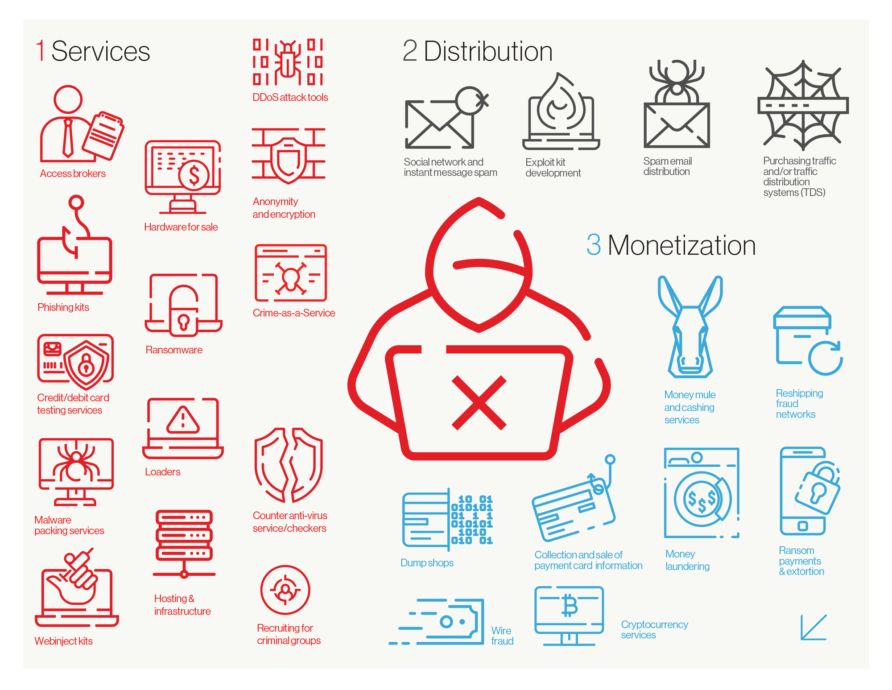
The eCrime Ecosystem
An extract from the Crowdstrike report.